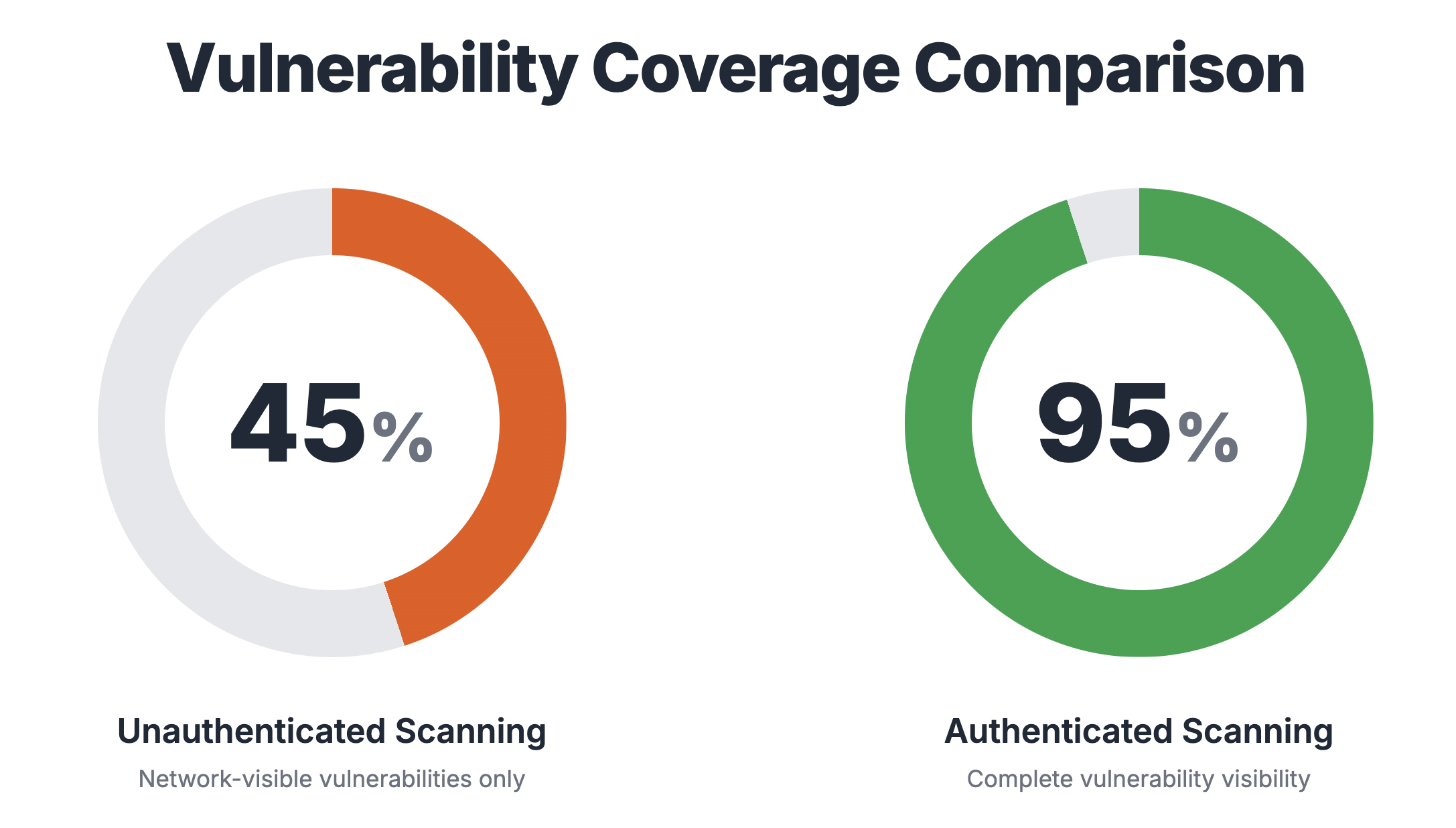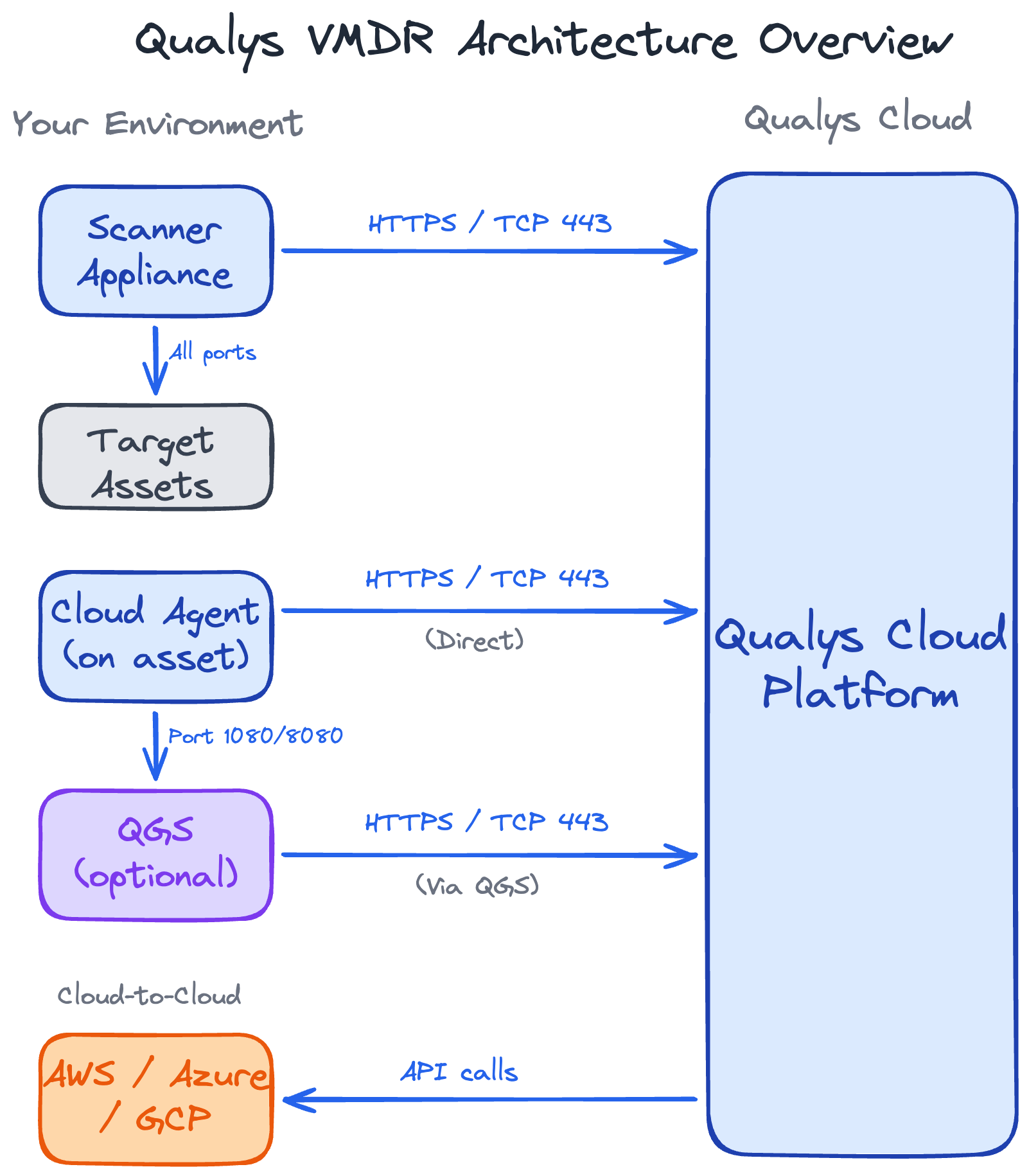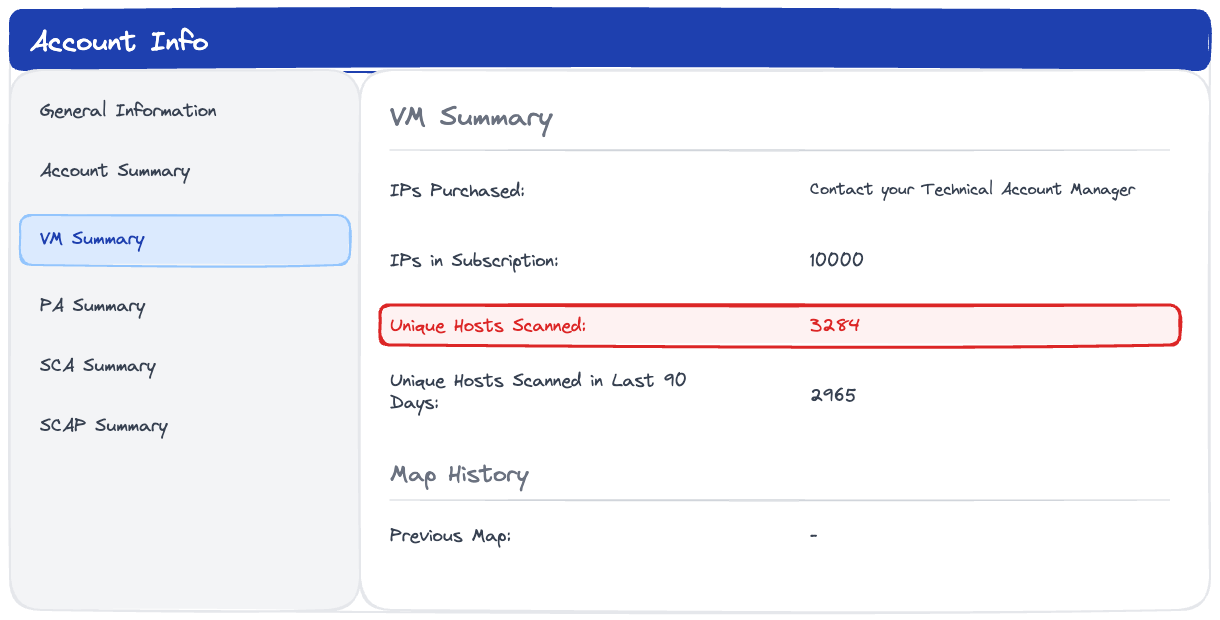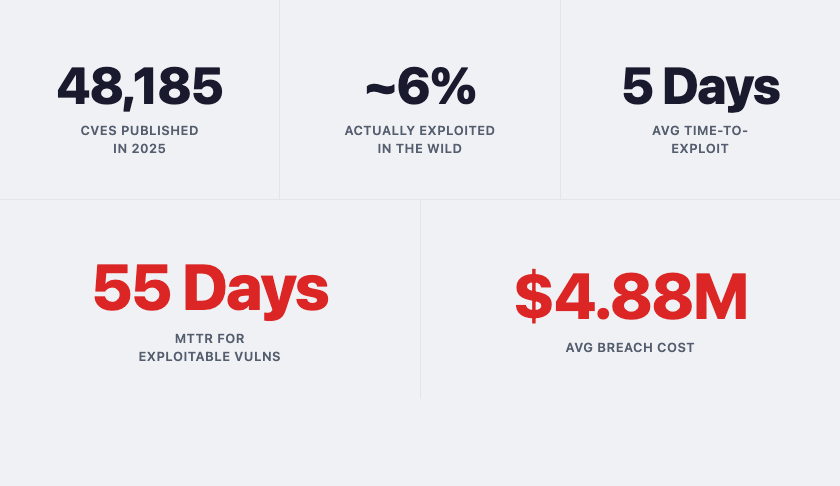
The Business Case for Risk-Based Vulnerability Prioritization
Patching everything is a losing strategy. Discover why your security team is fixing the wrong vulnerabilities — and what leadership can do about it. A framework for risk-based prioritization that reduces exposure without adding headcount.